Launch VM
Introduction
Welcome to our guide on configuring on-demand virtual machines with H100 GPU. You can create new vitual machines from here
Accessing Your Virtual Machine
Once launched, your VM will be available under the "Instances" section on the Dashboard page.
SSH Access
- Click the SSH button to copy the SSH command.
- Open your computer's terminal and paste the copied command to connect.
- The SSH command will look like this:
ssh cloud@xxx.xxx.xxx.xxx - No password is required as authentication is done via SSH keys.
Note: If you have chosen a custom location to store your SSH key, then do not forget to add the location as -i path while connecting to Jarvislabs.ai machines.
ssh -i /path/to/your/key/id_rsa -p port_number domain_name
Preparing Your VM
Update apt package manager
sudo apt update
Setting Up JupyterLab
Run the below command to install pip (Python Package Manager)
- Install pip (Python Package Manager):
sudo apt install pip -y
- Install JupyterLab:
pip install jupyterlab
- Launch JupyterLab in terminal:
export PATH=~/.local/bin:$PATH
env HOME=/home/cloud jupyter lab --ip=0.0.0.0 --NotebookApp.token='<YOUR_SECRET_TOKEN>' --allow-root --port 8888 &
Replace <YOUR_SECRET_TOKEN> with a secure token of your choice.
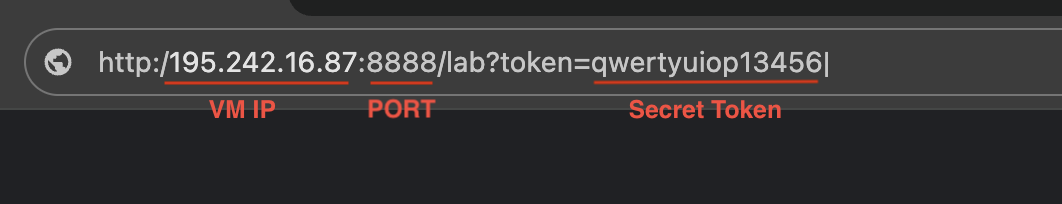
- Access JupyterLab in your browser using the URL:
http://<YOUR_VM_IPV4>:8888/lab?token=<YOUR_SECRET_TOKEN>
Replace <YOUR_VM_IPV4> with your VM's IP address and <YOUR_SECRET_TOKEN> with the token you set.
Accessing JupyterLab Securely via SSH Tunnel
For enhanced security, you can access JupyterLab through SSH tunneling instead of exposing it directly to the internet. This method encrypts all traffic through SSH.
- First, enable SSH tunneling on your VM by running these commands:
sudo sed -i 's/^#\?AllowTcpForwarding.*/AllowTcpForwarding yes/' /etc/ssh/sshd_config
sudo systemctl reload sshd
- Launch JupyterLab without exposing it to external connections:
jupyter lab --no-browser --port=8888
- On your local machine, create an SSH tunnel (open a new terminal window):
ssh -L 8888:localhost:8888 cloud@xxx.xxx.xxx.xxx
Replace xxx.xxx.xxx.xxx with your VM's IP address. If using a custom SSH key:
ssh -i /path/to/your/key/id_rsa -L 8888:localhost:8888 cloud@xxx.xxx.xxx.xxx
- Access JupyterLab in your local browser using:
http://localhost:8888
Note: With SSH tunneling, you don't need to allow port 8888 through UFW since JupyterLab is only accessible through the encrypted SSH tunnel.
Securing Your Instance with Firewall (UFW)
Basic Configuration
- First, ensure SSH access is allowed (do this BEFORE enabling UFW to avoid being locked out):
sudo ufw allow ssh
# Alternative if using custom SSH port
# sudo ufw allow 2222/tcp
- Set default policies:
sudo ufw default deny incoming
sudo ufw default allow outgoing
- Enable UFW:
sudo ufw enable
- Verify the status:
sudo ufw status verbose
Opening Additional Ports
To expose a service, use the following syntax:
# Allow specific port
sudo ufw allow 80/tcp # For HTTP
sudo ufw allow 443/tcp # For HTTPS
### Allow port by service name
sudo ufw allow http
sudo ufw allow https
Common Examples
- Allow MySQL/MariaDB:
sudo ufw allow 3306/tcp
- Allow PostgreSQL:
sudo ufw allow 5432/tcp
Managing Rules
- List numbered rules:
sudo ufw status numbered
- Delete a rule by number:
sudo ufw delete [number]
Security Tips
- Only open ports that are absolutely necessary
- Use specific IP addresses when possible:
sudo ufw allow from 192.168.1.100 to any port 22 - Regularly review active rules:
sudo ufw status - Always test SSH access before logging out after making changes